Digital signage usually makes headlines for all the right reasons — a stunning experiential installation, a next-gen innovation on the Vegas Strip or a groundbreaking event activation. But the recent unauthorized and disturbing video incident at the U.S. Department of Housing and Urban Development (HUD) is a sobering reminder: when security fails, the story becomes one of breach, not brilliance.
For system integrators, this is more than a cautionary tale. It’s a call to action. Whether facing an external attack or an insider threat, enterprise clients rely on you to ensure their digital signage networks are locked down and bulletproof. Security can’t be an afterthought — it must be architected from the ground up.
When managing digital signage at scale, an enterprise-grade content management system (CMS) gives integrators the control and security they need. It ensures reliable, compliant communication across all locations with features like role-based access, content-specific security settings, screen-level permissions and approval workflows — all designed to protect content before it appears on screen.
Define User Roles
The first consideration when granting team members access to a digital signage network is a fundamental one: “What should each person be allowed to do?” Roles across the network often require different levels of access, making it essential to strike a balance — empowering users to carry out their tasks efficiently while ensuring oversight through approval workflows and access controls.
Modern CMS platforms support a range of user roles that define actions individuals can take within the digital signage network. Assigning appropriate roles helps administrators ensure each user can access only the capabilities needed for their responsibilities. The tables below provide examples of common roles and their associated permissions.
CMS platforms also allow for role customization across different products or modules. For example, someone designated as an Approver for an employee communication application (ECA) doesn’t necessarily need the same level of access across the broader digital signage network.
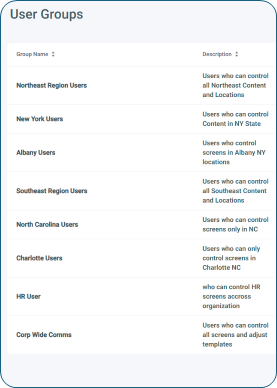
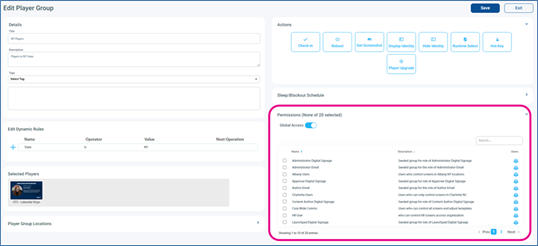
Manage User Groups and Permission-Based Access
The second key consideration is access to specific screens and content. For example, an approver responsible for one location may not need control over others. Which players should a content approver be able to manage? Which designs should a content author be allowed to edit? User groups and permission-based access help define where each user can apply their assigned actions, ensuring precise control across the network.
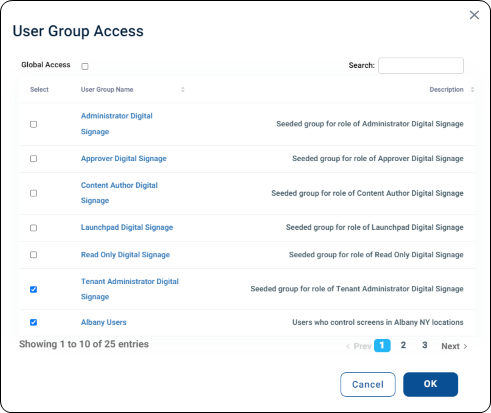
Administrators may wish to segment users based on geography, role or a combination of factors. Individual users can belong to multiple groups as needed. These groups are then used to secure access to specific content and players within the CMS.
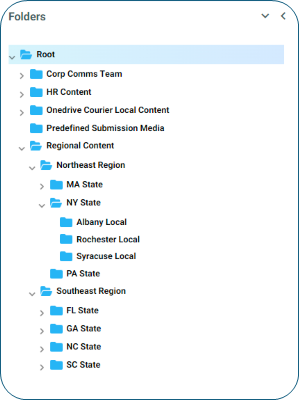
Organize Content with Folder-Based Access
Most CMS platforms use a familiar folder-based structure to organize and manage media items, layouts, templates and playlists. Organizing folders by region, department or use case makes it easier to align access permissions with specific user groups. The folder structure can be customized to align with the organization’s security requirements, ensuring the right people have access to the right assets.
Each folder can be assigned a unique set of user groups, while others may remain open with global access — reserving restrictions for critical content. This flexibility allows administrators to tailor permissions to the organization’s specific requirements.
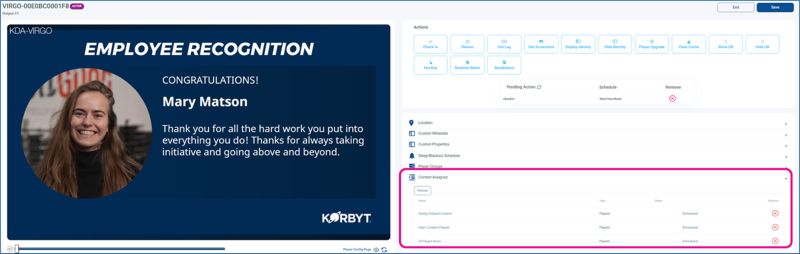
Enable Contributions Without System Access
Beyond folder-based and user role-based access, there are scenarios where it’s best to allow employees or external contributors to provide content without granting them direct access to the CMS.
A web-based submission interface offers a secure way to gather content without granting direct system access. Using predefined templates, team members can submit communications in draft form, which is then reviewed, approved and scheduled by users with Approver-level access or higher — ensuring oversight without compromising security.
Secure Access to Players
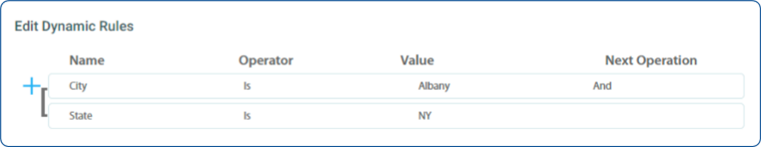
Before content reaches the screen, it’s essential to control who can assign it to specific players. When creating or editing a playlist, users can assign it only to the media players they’re authorized to access. Player groups enable administrators to limit access to specific user groups based on geography, use case or any other relevant criteria. These groups can be configured manually (statically) or dynamically using metadata assigned to individual players offering flexibility and precise control over how content is deployed across the network.
Each player group can be matched to the appropriate user groups to control who can view and manage those players within the system.
A user’s ability to make changes depends on two factors: their assigned role and the specific content and players they’re permitted to access.
Respond Quickly to Content Issues
While it’s critical to have protections in place for key systems, it’s equally important to have tools that enable a rapid response when incorrect or inappropriate content appears on screen. Whether caused by user error or malicious action, a powerful CMS offers simple and effective ways to remove unwanted content with minimal effort.
If a swift and wide-reaching response is required, administrators can use the Player Settings or Player Group screens to remove entire playlists from affected devices. Once addressed, normal content can be quickly restored to resume regular operations.
If a more targeted fix is needed, individual playlists can be reviewed to remove only the specific content in question. Alternatively, specific items can be deleted from the central Media Manager and players can be prompted to refresh their content using a check-in command. All of this can be done remotely — no need to physically access the media player.
In today’s increasingly connected environments, enterprises can’t afford to take digital signage security lightly. With the proper CMS in place, businesses can protect brand integrity, maintain trust and ensure seamless, real-time communication. By implementing a cloud-based CMS with customizable automation, role-based access and permission controls, integrators can help their clients stay secure, responsive and always ready to deliver.
Travis Kemp is VP of Product Management at Korbyt